Wednesday, March 11, 2015
Building an Enterprise File Server on Google Drive
Google Drive is increasingly popular in the enterprise, and many organizations would like to leverage it as a replacement for their existing on-premises file servers. Moving physical file servers to Drive provides many benefits, such as reliability, cost-effectiveness and the ability to access the files from anywhere and any device. However, the storage structure of Google Drive, where files are owned by many different users, is significantly different from the centralized organization of a file server, where everything is under the control of a small number of system administrators.
To address this problem, AODocs uses the Google Drive API to automatically transfer the ownership of files to a system account, and thus create a sort of “managed area” within Google Drive. With the Google Drive API, AODocs has complete control over the folder structure and the permissions of files owned by this system account. AODocs can be deployed in one click from the Google Apps Marketplace, which makes our application visible (and easy to try out!) for every Google Apps administrator in the world.
Companies who want to store their files on Google Drive may be concerned about losing control of their data (e.g. access to files being lost when an employee leaves the company) and controlling sharing permissions.
AODocs uses a single system account (i.e. a Google Apps account belonging to the customer’s domain, but not used by any human person) as a “proxy” to control the files. When a Google Drive files is added to an AODocs library, the ownership of the file is transferred to the AODocs system account and the file’s writersCanShare attribute is set to false, so that only AODocs is able to modify the file’s permissions afterwards.
To change the ownership of the file, we check if the system account can already access the file, and then either insert a new “owner” permission on it or use the Permissions.update method with the transferOwnership flag:
public void changeOwner(String user, String fileId, String newOwner) {
// Find what is the current permission of the new owner on the file
Permission newOwnerPermission = null;
PermissionList permissionList = RetriableTask.execute(new DrivePermissionListTask(drive.permissions().list(fileId)));
newOwnerPermission = findPermission(permissionList, newOwner);
if (newOwnerPermission == null) {
// New owner is not in the list, we need to insert it
newOwnerPermission = new Permission();
newOwnerPermission.setValue(newOwner);
newOwnerPermission.setType("user");
newOwnerPermission.setRole("owner");
Drive.Permissions.Insert insert = drive.permissions().insert(fileId, newOwnerPermission);
RetriableTask.execute(new DrivePermissionInsertTask(insert));
} else {
// New owner is already in the list, update the existing permission
newOwnerPermission.setRole("owner");
Drive.Permissions.Update update = drive.permissions().update(fileId, newOwnerPermission.getId(), newOwnerPermission);
update.setTransferOwnership(true);
RetriableTask.execute(new DrivePermissionUpdateTask(update));
}
}
Since all the files are owned by the system account, AODocs completely controls the lifecycle of the file (how they are created, in which folder they are located, who can change their permissions, who can delete them, etc). AODocs can thus provide higher-level document management features on top of Google Drive, such as configuring the retention time of deleted files, limiting external sharing to a whitelist of “trusted external domains”, or recording an audit log of file modifications.
As illustrated in the code snippet above, AODocs relies on the Google Drive API to perform all the operations on the managed files. The main challenge we had when using the Drive API was to properly handle all the error codes returned by the API calls, and make sure we make the difference between fatal errors that should not be tried again (for example, permission denied on a file) and the temporary errors that should be re-tried later (for example, “rate limit exceeded”). To handle that, we have encapsulated all our Google Drive API calls (we are using the Java client library) into a class named RetriableTask, which is responsible for handling the non-fatal errors and automatically retry the API calls with the proper exponential back-off. Here is a simplified version:
public class RetriableTaskimplements Callable {
[...]
private final Callabletask;
[...]
@Override public T call() {
T result = null;
try {
startTime = System.currentTimeMillis();
result = task.call();
} catch (NonFatalErrorException e) {
if (numberOfTriesLeft > 0) {
// Wait some time, using exponential back-off in case of multiple attempts
Thread.sleep(getWaitTime());
// Try again
result = call();
} else {
// Too many failed attempts: now this is a fatal error
throw new RetryException();
}
} catch (FatalErrorException e) {
// This one should not be retried
Throwables.propagate(e);
}
return result;
}
AODocs is designed to work seamlessly with Google Drive, and our top priority is to leverage all the integration possibilities offered by the Google APIs. We are very excited to see that new features are added very often in the Admin SDK, the Google+ API, the Drive API that will allow AODocs to provide more options to system administrators and improve the experience for our end users.
| Thomas Gerber profile Thomas is the CTO of Altirnao. Before founding Altirnao, Thomas has led a team of senior technologists and architects on High Availability/High Performance implementations of enterprise software. |
Friday, February 13, 2015
TeamViewer v9 0 23724 Server Enterprise full version with crack

Today, TeamViewer announces a new beta version of its popular remote control software for Windows, Mac and Linux PCs. The latest release, named TeamViewer 9 Beta, introduces new features aimed at businesses, developers and end-users as well as security improvements.
The most noteworthy security addition in TeamViewer 9 Beta is two-factor authentication. It allows users to add an extra layer of protection to their accounts by using security codes, that can be sent to their mobile devices and, alternatively, generated by dedicated mobile apps. On Macs, TeamViewer 9 also adds the option to increase the password strength in QuickSupport.
"TeamViewer has always been focused on remote support functionality", says the companys head of product management Kornelius Brunner. "With TeamViewer 9, we are going back to the roots and offering even better features for support teams in companies large and small".
Service Queue is a new TeamViewer 9 Beta feature aimed at IT staffs, that provides the option to assign, manage and share requests for immediate support. Users who join remote support sessions can now use a unique code, that is created specifically for that session, instead of having to exchange a username and password. The unique code can be distributed as a link.
The software adds the option to save customized customer modules with the companys branding (for Host, QuickJoin or QuickSupport) in the TeamViewer Management Console. The modules can be tailored, as needed, to a customer, group or support provider. The customers will receive the latest TeamViewer version, following any modifications.
TeamViewer 9 Beta introduces tab support. This allows users to open multiple remote control sessions and view multiple displays in a single window. Tabs can flash, indicating new activity.
Wake-on-LAN is now supported, allowing users to trigger a remote wake of the PCs they wish to control. The feature only works between devices connected to the same local network.
In TeamViewer 9 Beta users can take advantage of a univeral clipboard, which allows them to copy and paste content from their current device to a remotely-controlled one (files, folders, text and tables are supported). The formatting is carried over.
Using an FTP server, the software allows users to send files to devices and contacts without initiating remote control sessions. This offers an alternative to cloud-based storage services in such instances.
Specifically for Mac users, TeamViewer 9 Beta also adds the file box for quick sharing while using the software and the option to add a disclaimer when creating customized QuickSupport modules, which users have to accept before launching the software.
TeamViewer 9 Beta informs users of any new notifications in the Computers & Contacts area. The notifications include alerts for TeamViewer monitoring, ITBrain, new service cases, new contact requests and service cases assigned to the user. Read more

Windows Server 2003 Password Policy Changes

Windows cannot set the password for (user) because: The password does not meet the password policy requirements. Check the minimum password length, password complexity and password history requirements.
This error is because the password you or the user has tried to enter does not meet the password policy set in Windows Server 2003.
As a Server Administrator, you may find yourself in a situation where you need to change this policy, for more complex or simpler passwords to appease corporate users. Below are the default password policy requirements.
Minimum password length:
This security setting determines the least number of characters that a password for a user account may contain. You can set a value of between 1 and 14 characters, or you can establish that no password is required by setting the number of characters to 0.
Default:
7 on domain controllers.
0 on stand-alone servers.
Password Complexity Requirements:
Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
Be at least six characters in length
Contain characters from three of the following four categories:
English uppercase characters (A through Z)
English lowercase characters (a through z)
Base 10 digits (0 through 9)
Non-alphabetic characters (for example, !, $, #, %)
Complexity requirements are enforced when passwords are changed or created.
Default:
Enabled on domain controllers.
Disabled on stand-alone servers.
Maximum password age:
This security setting determines the period of time (in days) that a password can be used before the system requires the user to change it. You can set passwords to expire after a number of days between 1 and 999, or you can specify that passwords never expire by setting the number of days to 0. If the maximum password age is between 1 and 999 days, the Minimum password age must be less than the maximum password age. If the maximum password age is set to 0, the minimum password age can be any value between 0 and 998 days.
Note: It is a security best practice to have passwords expire every 30 to 90 days, depending on your environment. This way, an attacker has a limited amount of time in which to crack a user’s password and have access to your network resources.
Default: 42.
To Change the Default Password Policy in Windows Server 2003
Select Domain Security Policy from Administrative Tools.
Click on Security Settings > Account Policies > Password Policy.
Right-click on Passwords must meet complexity requirements.
Click Properties from the context menu.

Do not remove the check from the Define this policy setting checkbox.
Select the Disabled option.
(This will allow less complex passwords)
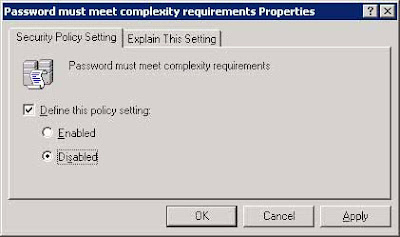
Double-click on Minimum Password Length in the right pane.
Enter a new minimum password length. Entering Zero (0) will remove the password requirement.
Do not remove the check from the Define this policy setting checkbox.
Click the OK button.

Close the Default Domain Security Settings window.
Type gpupdate /force at the Command Prompt. This will refresh the security policy without restarting.
Press the Enter.

For more info visit;
http://www.iishacks.com/index.php/2007/09/24/windows-server-2003-password-policy-changes/